Securing Input and Output Processes on The Web to Minimize SQL-Injection and XSS Attacks Using IDS and IPS Methods
Pengamanan Proses Input Output Pada Web Untuk Meminimalisir Serangan SQL-Injection Dan XSS Menggunakan Metode IDS Dan IPS
DOI:
https://doi.org/10.21070/joincs.v4i1.1577Keywords:
Security, injection, IDS IPS, regular expressionAbstract
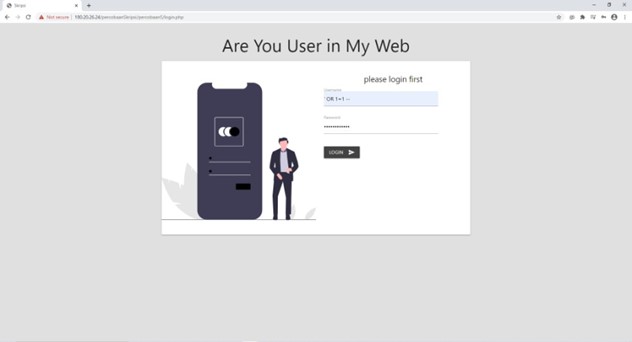
Some of the gaps that exist in web applications are often encountered, such as input both in the input form and input in the url. One of the attacks that are often found in data input is SQL-injection and XSS. Therefore one of the precautions is to carry out data security measures in the input and output process. Here the author uses the IDS and IPS methods as security of input forms from SQL-injection and XSS attacks. IDS is used as a detection and recording of attacks while IPS functions as a blocking access to the website if SQL-injection and XSS attacks are detected. In this case filtering uses the preg_match () function where the writer inserts the word into preg_match () as a rule which later if the user inputs what is in the preg_match () rule then the user is trying to do an injection attack. The data retrieved by the IDS script are ip_address, injected files, scripts, browsers used. IPS uses ip_address as a rule to block access from users when doing injection. It is hoped that the IDS and IPS scripts created will help secure the input output process that is on the web in order to minimize the occurrence of SQL-injection and XSS attacks.
References
[2] AON Cyber Solutions, “2019 Cyber Security Risk Report: What’s Now and What’s Next,” no. February, pp. 1–23, 2019.
[3] A. Tajpour and M. J. Z. Shooshtari, “Evaluation of SQL injection detection and prevention techniques,” Proc. - 2nd Int. Conf. Comput. Intell. Commun. Syst. Networks, CICSyN 2010, pp. 216–221, 2010, doi: 10.1109/CICSyN.2010.55.
[4] A. S. Irawan, E. S. Pramukantoro, and A. Kusyanti, “Pengembangan Intrusion Detection System Terhadap SQL Injection Menggunakan Metode Learning Vector Quantization,” J. Pengemb. Teknol. Inf. dan Ilmu Komput. Univ. Brawijaya, vol. 2, no. 6, pp. 2295–2301, 2018.
[5] C. Taylor and S. Sakharkar, “DROP TABLE textbooks: An argument for SQL injection coverage in database textbooks,” SIGCSE 2019 - Proc. 50th ACM Tech. Symp. Comput. Sci. Educ., no. 3, pp. 191–197, 2019, doi: 10.1145/3287324.3287429.
[6] BSSN, “Mengenal Sql Injection,” Bssn, 2019, [Online]. Available: https://bssn.go.id/wp-content/uploads/2019/09/Proteksi-terhadap-Kerentanan-SQL-Injection-2019-v.1.3.1_sign.pdf.
[7] A. Tajpour, M. Masrom, M. Z. Heydari, and S. Ibrahim, “SQL injection detection and prevention tools assessment,” Proc. - 2010 3rd IEEE Int. Conf. Comput. Sci. Inf. Technol. ICCSIT 2010, vol. 9, no. July 2014, pp. 518–522, 2010, doi: 10.1109/ICCSIT.2010.5563777.
[8] R. U. Putri and J. E. Istiyanto, “Analisis Forensik Jaringan Studi Kasus Serangan SQL Injection pada Server Universitas Gadjah Mada,” IJCCS (Indonesian J. Comput. Cybern. Syst., vol. 7, no. 1, 2013, doi: 10.22146/ijccs.2157.
[9] C. Cetin, D. Goldgof, and J. Ligatti, “SQL-Identifier Injection Attacks,” 2019 IEEE Conf. Commun. Netw. Secur. CNS 2019, pp. 151–159, 2019, doi: 10.1109/CNS.2019.8802743.